Setting Up A Second AWS Account With AWS Organizations
Contents
In this post I’ll be creating a second AWS account using AWS Organizations. But first of all I should probably explain why!
I’m looking to improve my backup strategy. I currently make use of Google Drive for most of my small and regularly used files, and once a month I copy my larger and seldom-used files to an external HD that I keep offsite. This process has several inherent problems, including:
- I can easily lose data between backups
- If my external HD fails I lose my backups
- If something bad happens while the laptop and HD are together I lose everything
So it make sense to start using S3. I have lots of large files, including WAVs, FLACs and MP4s, that will never change and are infrequently used - an ideal use case for S3’s object-based storage and various storage classes. But I still have concerns over security - if someone or something hacks or otherwise incapacitates my AWS account then all my data is gone. Not an issue if I keep a local copy of the files, but ideally I want most of this stuff off my laptop.
The solution is to have two AWS accounts and have them set up for cross-account replication. That way one bucket’s contents are replicated to another bucket in a completely separate account - if anything unfortunate then happens to one account then the other is completely unaffected. This will mean I effectively double my AWS storage bill, but when we’re talking $0.023 per GB on S3 Standard I think I can take the hit in exchange for the increased security. So what’s the best way to go about creating this new account? Enter AWS Organizations.
AWS Organizations is an account management service that allows the creation and consolidation of multiple AWS accounts into an organization that can be centrally managed and controlled from one ‘master’ account. Today I’ll be using it to set up a new organization and create an account within it. I start by logging onto the AWS console and selecting AWS Organizations. On the next screen I choose Create Organization:
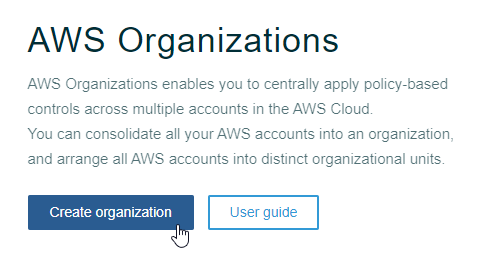
This sets my account as the master account for the organization, but before I can proceed I must validate my email address:
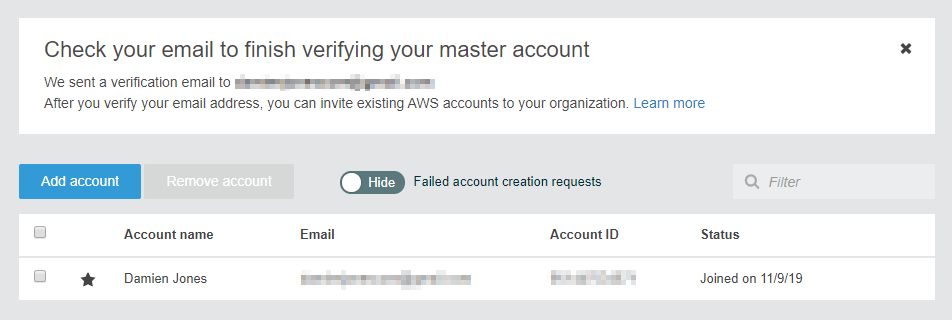
AWS send an email to the email address associated with the root account:
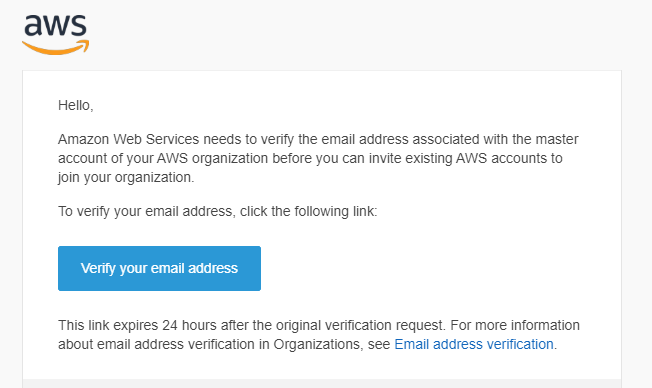
Following the instructions in the email will verify my account as the master account for my organization:
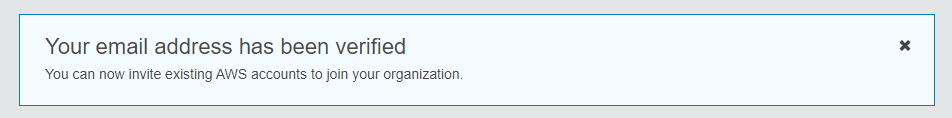
The master account has the responsibilities of a payer account and is responsible for paying all charges that are accrued by the member accounts. Once chosen it cannot be changed. The master account of an organization differs from the organization members in that it can:
- Invite other existing accounts to the organization
- Remove accounts from the organization
- Manage invitations
- Apply policies to entities within the organization
- Create accounts in the organization
With this groundwork done I can now create accounts that will automatically be part of my organization. From the AWS Organizations dashboard I click on Add Account, then Create Account. I am prompted for information about the new account:
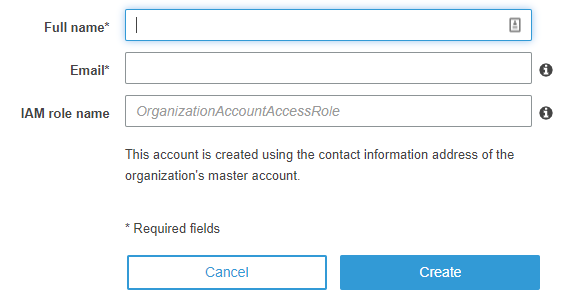
The IAM role being created here grants the organization’s master account permission to access the newly created member account. The IAM name is optional - if no name is specified AWS Organizations gives the role a default name of OrganizationAccountAccessRole. Note that the email address must be unique to the new account because it will be used to sign in as the root user. Once completed the dashboard is shown again with the new account in the process of being created:
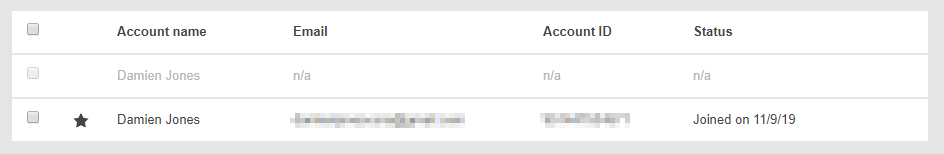
This soon changed when the account is active:
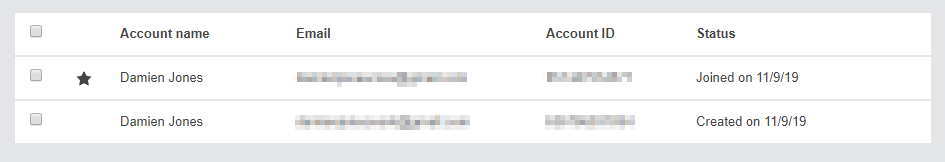
I’ve obfuscated the email addresses and Account IDs for security but they are different from one another.
Next time I’ll be accessing and administering the new account.
Thanks for reading ~~^~~
Author Damien Jones
LastMod 2019-11-07